Simplified Total Risk Management (STORM)
The Simplified Total Risk Management (STORM) Enterprise Risk Management (ERM) toolkit provides quantitative risk assessment, combined with tools and processes for asset valuation, threat assessment, vulnerability assessment, and control evaluation.
Manage Risk & Security for Less
- Risk assessment
- Risk management
Use Any Risk Management Framework (e.g. NIST 800-30, OCTAVE)
STORM ERM can stand alone, or may be used to simplify, support, and implement other risk management frameworks such as NIST 800-30 or OCTAVE.
| Method | Process | STORM Implementation |
|---|---|---|
NIST 800-30 |
General | Simplified Total Risk Management (STORM) |
| Prepare for the risk assessment | STORM Asset Valuation Process (SAVP) | |
| Identify threats, threat events, threat likelihood, and threat impacts | STORM Threat Assessment Process (STAP) | |
| Identify vulnerabilities | STORM Vulnerability Assessment Process (SVAP) | |
| Determine risks | Simplified Total Risk Management (STORM) | |
OCTAVE |
General | Simplified Total Risk Management (STORM) |
| Identify critical assets | STORM Asset Valuation Process (SAVP) | |
| Identify threats | STORM Threat Assessment Process (STAP) | |
| Identify organizational & technical vulnerabilities | STORM Vulnerability Assessment Process (SVAP) | |
| Develop protection strategy | STORM Control Evaluation Protocol (SCEP) |
Take Advantage of Quantitative Risk Assessment
Most risk management systems use qualitative1 risk assessment, but STORM offers true quantitative2 enterprise risk assessment & management (ERM).
Why Quantitative Risk Assessment?
- More accurate and precise
- Better prioritization of remedial efforts
- Best of both worlds (qualitative labels can be applied to quantitative measurements, but not vice versa)
- Directly compare risk across assessments
1Quantitative risk assessment measures risk in dollars, percentage of asset value, or some other meaningful continuum. Quantitative risk values can be directly compared, manipulated mathematically, and analyzed statistically. Qualitative labels may be applied to quantitative values using ranges (i.e., more than 9% of asset value at risk may be considered HIGH risk).
2Qualitative risk assessment assigns arbitrary fixed values to risk factors, like LOW, MEDIUM, and HIGH, 1 through 5, etc. Qualitative values have intuitive meaning, but cannot be directly compared (there may be substantial differences in risk between two MEDIUM risk factors, for example), cannot be manipulated mathematically, and can only be analyzed in terms of counting risk factors in each qualitative category
Manage All Classes of Risk
STORM allows you to manage information technology and information security risk. But you can also use STORM to integrate and manage all classes of operational, casualty, financial, and strategic risk, providing a true Enterprise Risk Management (ERM) capability.
Get Actionable Results Quickly
Other quantitative risk management techniques require significant data entry and analysis efforts before producing any results. STORM overcomes this limitation.
STORM uses successive approximation to produce actionable, quantitative results with the same data entry effort as qualitative models. For example, STORM can estimate information security risk with only vulnerability information. Over time, you can add threat, asset, and control information, and the results will become successively more precise.
The following chart is an example of risk estimation using only vulnerability information (the chart is based on actual STORM vulnerability information collected automatically over a period of 25 months). The vulnerability measurements clearly demonstrate the increased risk related to major technical vulnerabilities like HeartBleed and ShellShock.
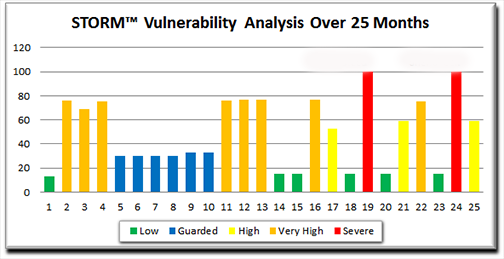
Compare Risk Over Time
STORM's quantitative risk information can be directly compared from one risk analysis to the next, and from one organization to the next.
This chart demonstrates how STORM can be used to track your own risk, and to compare your risk against other similar organizations (this chart is based on actual data from 16 risk assessments conducted over a one-year period).
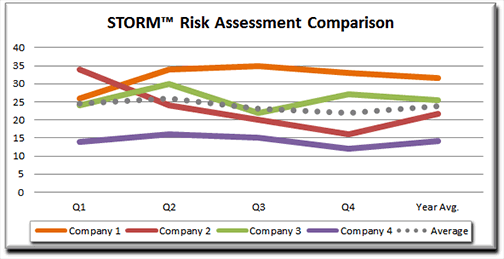
Easily Identify the Sources of Excessive Residual Risk
All STORM measurements can be directly compared and manipulated mathematically. This characteristic allows you to roll up (aggregate) multiple risk factors into a single quantitative value that applies to your entire organization, department, or other organizational unit. Or, you can drill down to increasing detail to find the primary sources of that risk.
Below is an example of this capability. Sample Company has a total residual organizational risk of 21 RU. Click on the arrowhead next to each name to expand the organizational tree and find out which assets are at the greatest risk.
| Organizational Unit or Asset Group | Risk |
|---|---|
| Sample Company | 21 |
| Information Technology | 19 |
| Internet Presence | 2 |
| Critical Information Systems | 8 |
| Other Internal Systems | 17 |
| Human Resources | 7 |
| Leadership | 5 |
| Management | 4 |
| Other Staff | 3 |
| Business Operations | 13 |
| Leadership & Governance | 4 |
| Enterprise Risk Management | 12 |
In this example, the areas of high risk within the organization are the Other Internal Systems (part of information technology) and Enterprise Risk Management (part of business operations).
Why Don't These Numbers Add Up?
Integrate With Existing Applications & Business Processes
STORM provides a software development toolkit (SDK) that allows you to integrate STORM risk management and the STORM Independent Ancillary Processes with your existing business processes.
STORM can be directly integrated with Java applications, web applications (HTML, CSS, JavaScript, and Ajax), Microsoft VBscript, and Microsoft Excel spreadsheets.
STORM can also be used to process information exported from any program or process in comma separated values (CSV) or XML formats.
Finally, RESCOR provides STORM software integration services, which provides extensive software engineering and business process expertise to integrate STORM with existing applications on any platform from mobile to mainframe.
Simplified Total Risk Management, STORM & StrongCOR are trademarks of RESCOR; RAPID & RSK are trademarks of Andrew T. Robinson.
